Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
All Topics
Security
Threat intelligence
Cyber Defense
Cryptography
Malware
Network Security


NIST CSF 2.0: Turn Cyber Risk into Business Clarity
NIST CSF 2.0 made practical: manage cyber risk, meet compliance, and align security with business outcomes, with clear steps from Current to Target.
NIST CSF 2.0 made practical: manage cyber risk, meet compliance, and align security with business outcomes, with clear steps from Current to Target.
TL;DR
- One language for security across C-Suite, IT and Ops
- Six functions to structure work: Govern, Identify, Protect, Detect, Respond, Recover
- From Current → Target profile, then close the gap with measurable steps
Introduction
Cyber risk is business risk. Fines, downtime, brand damage, especially when OT is involved. NIST CSF 2.0 gives you a practical model to align leadership, security, and operations.
Why it matters
- Win bigger deals. Many buyers require proof of security and compliance (e.g., ISO 27001). CSF helps you achieve it.
- Reduce regulatory stress. Map controls to NIS2, DORA and more—once, consistently.
- Run smoother. Clear roles, fewer hand-offs, faster MTTR. Less noise, more outcomes.
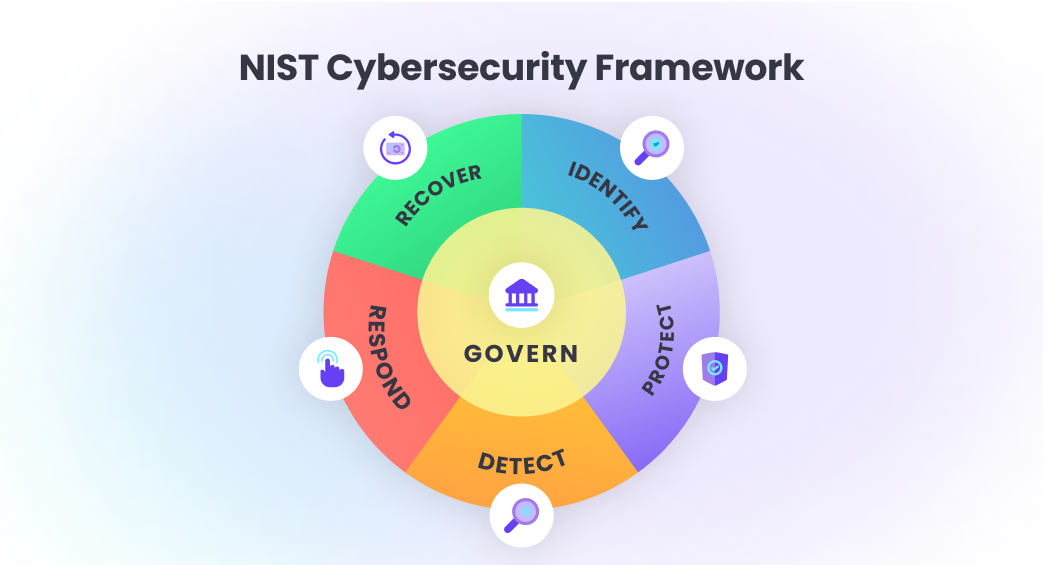
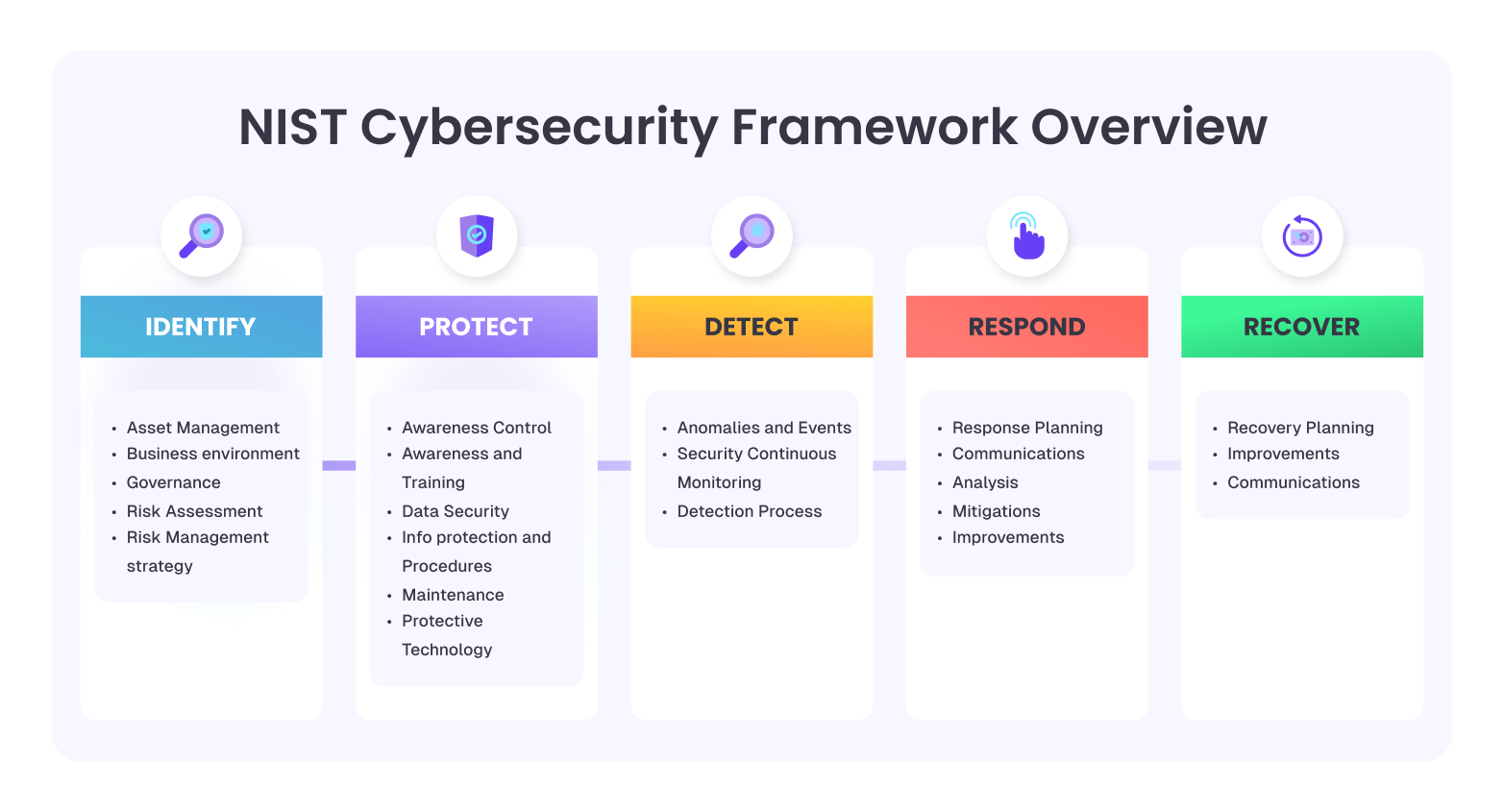
The six functions (at a glance)
- Govern. Set direction, ownership, KPIs, and risk appetite.
- Identify. Know assets, dependencies, obligations, and exposure.
- Protect. Access control, segmentation, hardening, training.
- Detect. Monitor, correlate, alert with context.
- Respond. Contain, analyze, communicate, and learn.
- Recover. Restore services fast and improve resilience.
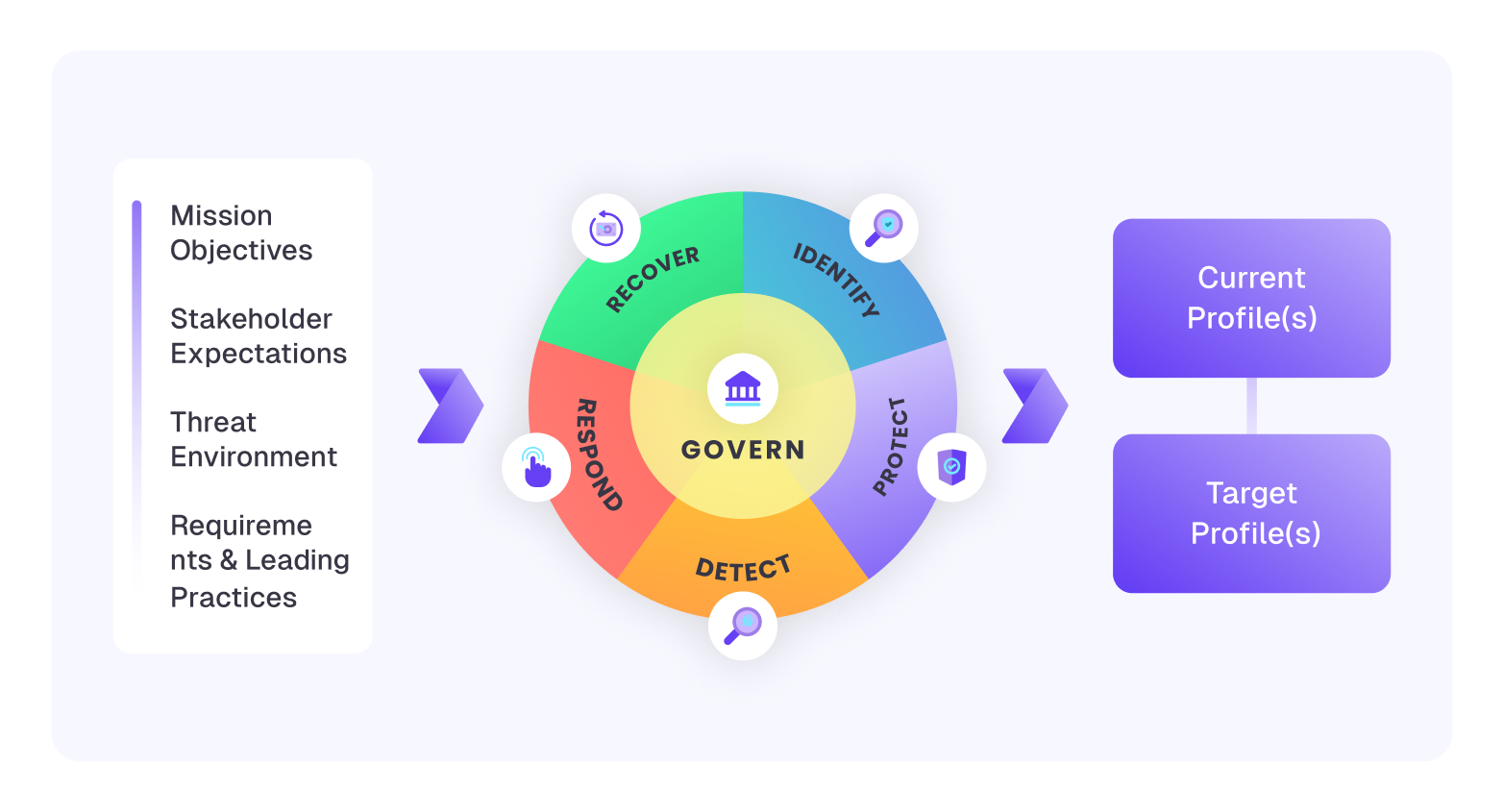
How to implement (fast)
- Current Profile. Where are you today? Tools, controls, processes, metrics.
- Target Profile. What outcomes do you need? Compliance, KPIs, coverage.
- Close the gap.
- Prioritize high-impact fixes (privileged access, vuln mgmt, IR basics).
- Execute in phases with milestones and owners.
- Review quarterly. Adjust as threats and business change.
Common pitfalls
- Checklist thinking. CSF is a program, not a pass/fail.
- No governance. Without ownership and KPIs, nothing sticks.
- Over-engineering. Start simple. Improve with data.
Where we help
We use CSF 2.0 to structure strategy, operations, and tooling so your security is audit-ready and run-ready.
If you want a quick start: our 8-hour assessment gives you a Current/Target view and a plain-English roadmap.
Want the template or a walkthrough? info@datadefend.com
No items found.
Stay Informed with DataDefend Insights
Subscribe to our newsletter by submitting your email.






