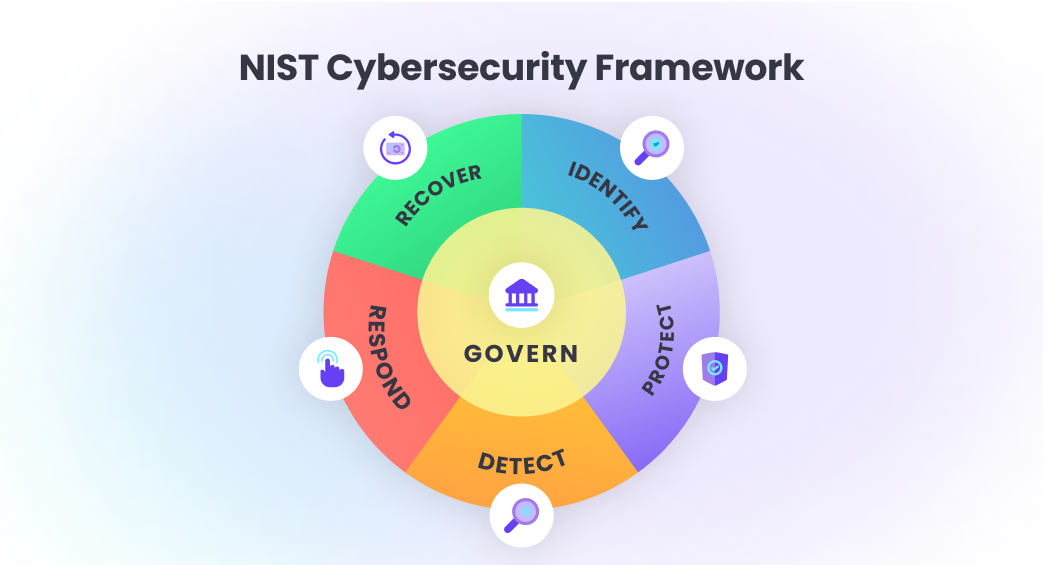
NIST CSF 2.0 made practical: manage cyber risk, meet compliance, and align security with business outcomes, with clear steps from Current to Target.
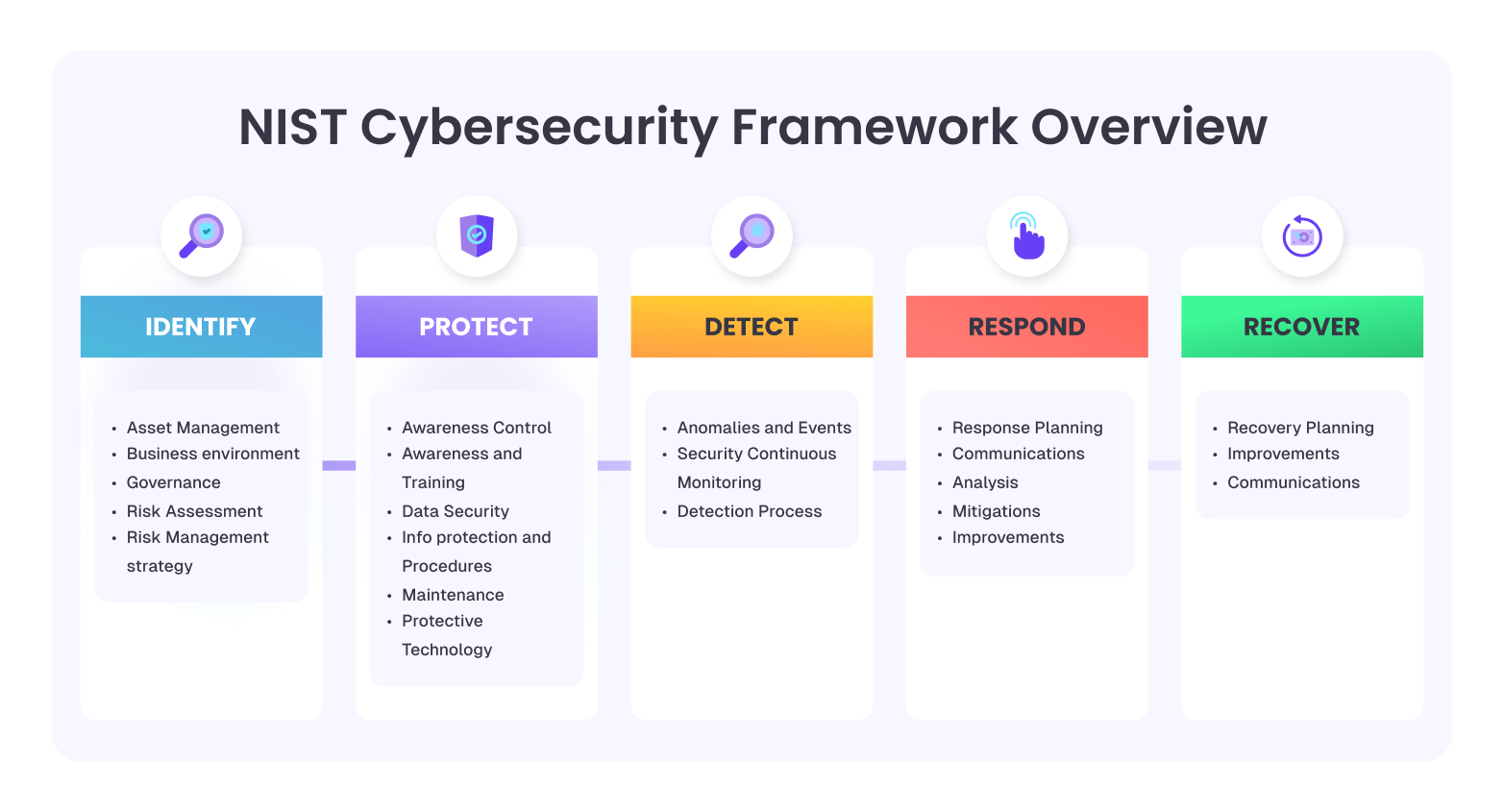
Cyber risk is business risk. Fines, downtime, brand damage, especially when OT is involved. NIST CSF 2.0 gives you a practical model to align leadership, security, and operations.
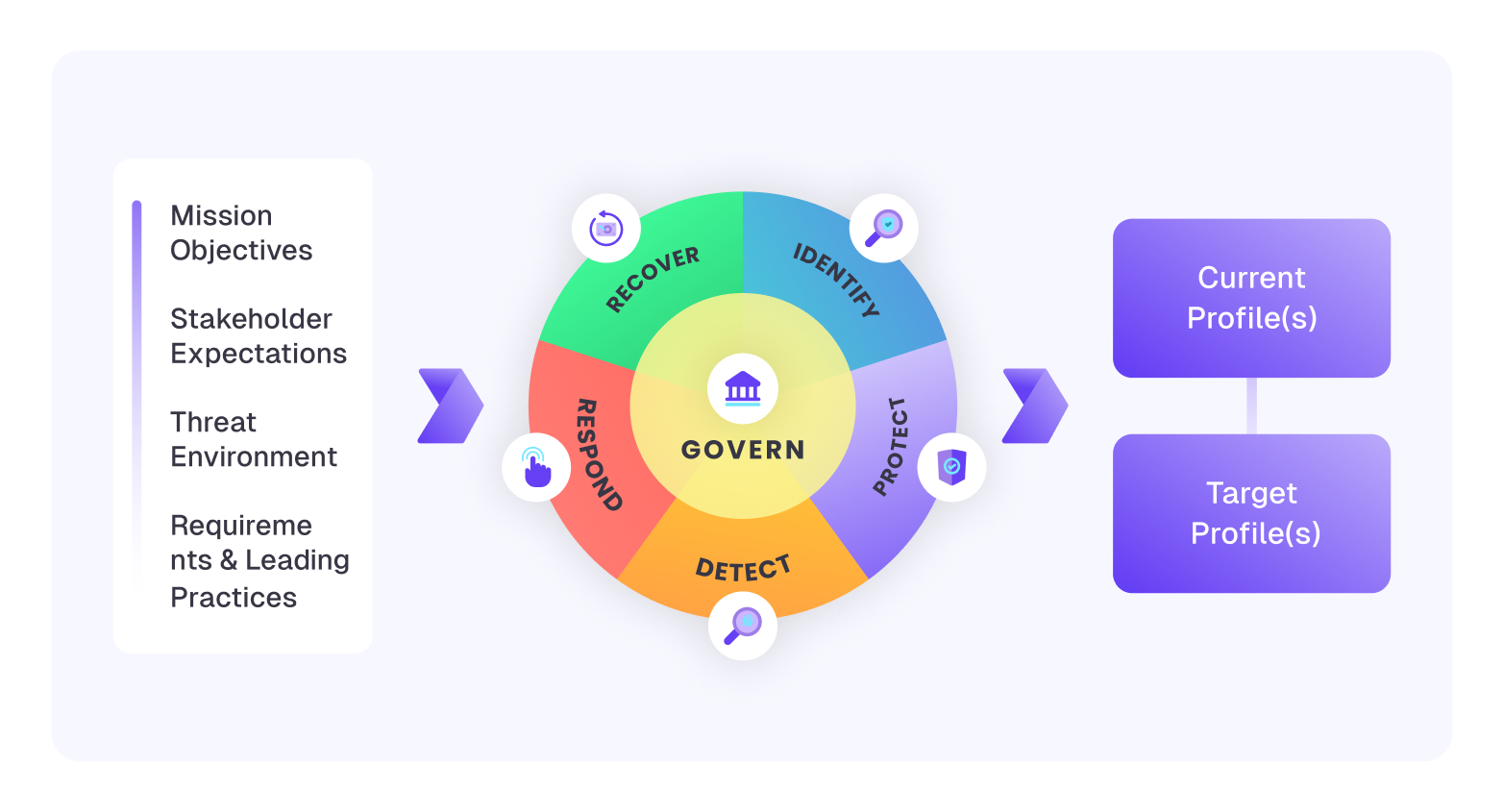
We use CSF 2.0 to structure strategy, operations, and tooling so your security is audit-ready and run-ready.
If you want a quick start: our 8-hour assessment gives you a Current/Target view and a plain-English roadmap.
Want the template or a walkthrough? info@datadefend.com



NIST CSF 2.0 made practical: manage cyber risk, meet compliance, and align security with business outcomes, with clear steps from Current to Target.

Cyber risk is business risk. Fines, downtime, brand damage, especially when OT is involved. NIST CSF 2.0 gives you a practical model to align leadership, security, and operations.

We use CSF 2.0 to structure strategy, operations, and tooling so your security is audit-ready and run-ready.
If you want a quick start: our 8-hour assessment gives you a Current/Target view and a plain-English roadmap.
Want the template or a walkthrough? info@datadefend.com
